I recently spent a largely sleepless night at a hotel, and out of equal parts curiosity and boredom, decided to kill some time scanning the guest network to see what my fellow travelers might be up to. As you’d probably expect, I saw a veritable sea of Samsung and Apple devices. But buried among the seemingly endless number of smartphones charging next to their sleeping owners, I found something rather interesting. I was as picking up a number of Amazon-made devices, all of which had port 5555 open.
As a habitual Android tinkerer, this struck me as very odd. Port 5555 is used for Android Debug Bridge (ADB), a development tool used to control and perform various administrative tasks on an Android device over the network or (more commonly) locally over USB. The number of users who would have legitimately needed to enable network ADB on their devices is surely rather low, so to see a half dozen of them on the network at the same time seemed improbable to say the least.
Why would so many devices manufactured by Amazon all have network ADB enabled? I realized there must be a connection, and it didn’t take long to figure it out.
The Seedy World of “Jailbroken” Fire Sticks
The somewhat awkwardly named “Fire TV Stick” is a cheap little device that you stick in the HDMI port of your TV to turn it into a “smart” TV. Ostensibly it allows you to stream content from all the big name providers out there, but realistically Amazon is hoping it will get you to spend more money within their ecosystem. For Amazon, the Fire Stick is to video content as the Kindle is to books: sell the hardware cheap, and make money on the subsequent content purchases.
That was the plan, anyway. But it didn’t take long for people to realize that the Fire Stick was running Amazon’s customized version of Android, and what’s more, was particularly easy to install additional software onto. As you might expect, a huge community of Fire Stick modifications and hacks sprung up in some of the less fashionable parts of the Internet, largely focused on turning the Fire Stick into the ultimate device for illicit video content.
How do you install this software, you might ask? It’s simple, and about a thousand different guides and YouTube videos will walk you through the process of “jailbreaking” your Fire Stick. All you need to do is go into “Developer Options” and enable “Apps from Unknown Sources” and “ADB Debugging”. These handy-dandy guides don’t bother to explain the dangers of doing this, nor do they caution the user to turn off these settings after they’ve installed the third party software of choice (usually Kodi).
The end result is a whole community of people using Amazon Fire TV Sticks in development mode, where anyone can connect to these devices over the network and gain full control over them. A potential botnet, created by willing participants.
Realistic Risk
To be fair, most of these Fire Sticks will never leave the user’s home. In such a situation, while there’s still no good reason to allow remote ADB on these devices, the risk is probably low enough that there’s no great danger to leaving it on. But if you’re using a “jailbroken” Fire Stick on a public network, such as a school dorm or hotel, you’re asking for trouble.
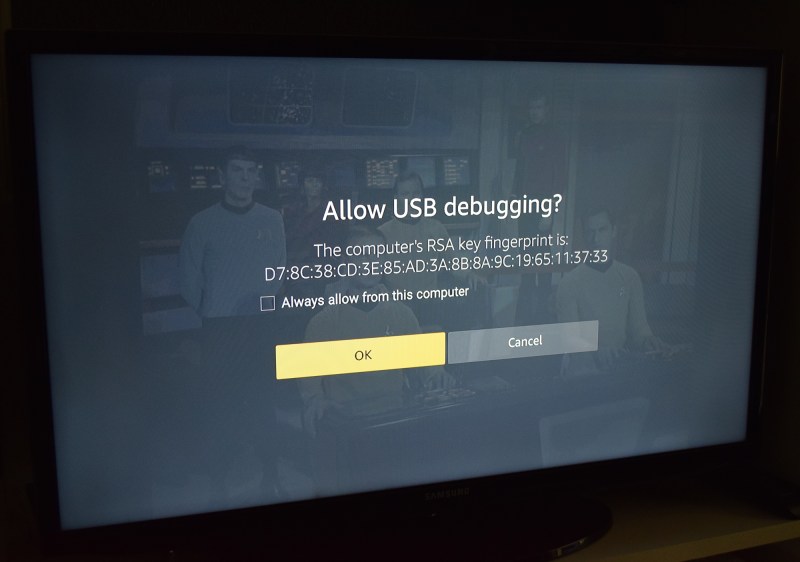
It should be said that the Fire Stick does pop up a message when a device tries to connect over remote ADB. But it’s not a terribly descriptive message, and certainly doesn’t tell the user what this big complicated string of characters means. It doesn’t even say that the connection is coming from a remote device. To add insult to injury, “OK” is the default action when the prompt comes up.
Frankly, it’s a pretty terrible “warning” message for the average user. Granted this message was never intended to show up during normal operation of the Fire Stick (remember, you must first enable “Developer Options” to get to this point), but still. The majority of people will simply press the “OK” button as fast as possible to get this scary Matrix-code off of their TVs so they can get back to watching Netflix.
Once the user hits “OK”, it’s game over. With ADB access approved, an attacker would be free to install and execute their own software, wipe the Fire Stick, or do basically anything else they wanted.
Sniffing for Fire Sticks
If you want to go on the hunt for ADB enabled Fire Sticks, the first thing you need to do is identify Amazon-manufactured devices on the network. There are many ways you could do this, but a quick one-line from a *nix machine with arp-scan installed would look something like: sudo arp-scan --localnet | grep Amazon. This would find the MAC addresses for all the devices on the local network, then pipe that to grep which would search the results for the word “Amazon”.
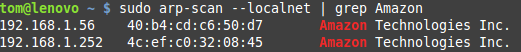 If it’s on the LAN and was made by Amazon, that should get you it’s IP address. The next step would be port scanning each of those IPs. Again there are plenty of ways to do this on different platforms, but
If it’s on the LAN and was made by Amazon, that should get you it’s IP address. The next step would be port scanning each of those IPs. Again there are plenty of ways to do this on different platforms, but nmap is always a good bet. Of course, if it’s only one or two devices you could always just try connecting to them directly with adb connect and seeing what happens.
While tinkering with this concept I’ve come up with a Python script which scans the local network for potentially vulnerable Amazon devices. This script could easily be expanded to actively connect to those devices and execute commands on them (such as rebooting the device), but for obvious reasons I’ll let that be an exercise for the reader.
The Takeaway
This is a perfect example of why you need to be exceptionally cautious when following guides posted online. Whether it’s due to ignorance or indifference, the individuals who create these clickbait “jailbreaking” guides for the Amazon Fire Stick don’t adequately explain the risks of enabling “Developer Options”, and the Fire Stick itself doesn’t do much better in terms of warning the average consumer about allowing remote devices to connect.
It’s also important to remember how sophisticated these “simple” media player devices are becoming. In the case of the Fire Stick, we’re talking about a full fledged computer running Android, and all that entails. It’s not outside the realm of possibility that your Fire Stick could be compromised with a Trojan horse style application, and then become a backdoor into your home network. What seemed like a cheap way to watch streaming movies could end up costing more than you bargained for.
TL;DR: Turn off remote debugging.